IoT applications connect devices that sense, process, and share data, enabling innovations such as remote patient monitoring, smart homes, and industrial automation. However, building a successful solution is complex, as hardware, cloud architecture, security, compliance, and UX must all align.
The global IoT security market is valued at $6.3 billion in 2024 and is projected to reach $42.9 billion by 2033, growing at a CAGR of 23.4%. This statistic shows that embedding security from the outset isn’t optional; it’s necessary.
This guide walks you through every stage of IoT application development. It covers architecture, prototyping, firmware, back-end, front-end, security, deployment, and lifecycle. You’ll find practical insights to help both business leaders and developers build scalable, secure, and compliant solutions.
Key Takeaways
- Layered Architecture: Build across four integrated layers—devices, connectivity, cloud, and application—for seamless and reliable IoT operations.
- Strategic Planning: Begin with clear objectives, well-defined use cases, and detailed functional and non-functional requirements. Address monetization and compliance early.
- Smart Tech Stack: Select sensors, communication protocols, platforms, and frameworks based on performance, scalability, and long-term support.
- Built-In Security: Secure the system from the outset with device authentication, data encryption, and compliance with regulations such as GDPR or HIPAA.
- User-Centric Design: Offer intuitive dashboards and real-time controls. Test the entire system under real-world conditions to evaluate its performance and usability.
- Scalability & Maintenance: Use cloud-native scaling, edge resilience, and OTA updates to keep your IoT system reliable and future-ready.
Understanding the IoT Ecosystem and Architecture
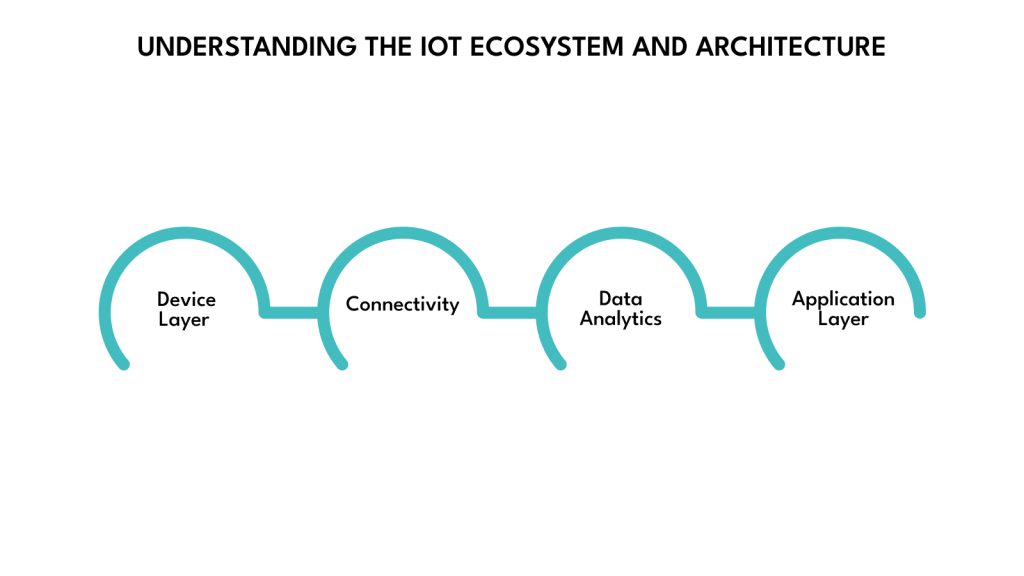
A complete IoT system is structured across four integrated layers: device, connectivity, cloud/data, and application. Each layer must be carefully designed to ensure seamless performance, security, and scalability.
1. Device Layer: Sensors, Actuators, and Firmware
This is the perception layer, where physical data is captured or actions are performed.
- Includes sensors (e.g., temperature, GPS, vibration) and actuators (e.g., motors, relays).
- Devices often run on microcontrollers (MCUs) that handle signal processing and data transmission.
- Firmware must be secure, modular, and designed for over-the-air (OTA) updates to enable remote maintenance.
- Hardware reliability and secure boot processes are critical to ensure long-term, stable operation.
2. Connectivity and Edge Computing
This layer transfers data from devices to the cloud and handles processing near the data source.
- Connectivity options include Wi-Fi, BLE, cellular (4G/5G), Zigbee, LoRaWAN, NB-IoT, and RFID.
- Gateways or edge devices may sit between sensors and cloud services.
- Edge computing processes data locally to reduce latency, save bandwidth, and maintain functionality during outages.
- Example: An edge device can run lightweight AI models to detect anomalies and only forward insights to the cloud.
Choose protocols and compute locations based on latency, bandwidth, power constraints, and reliability requirements.
3. Cloud and Data Analytics Layer
This layer manages data ingestion, storage, analytics, and system integration.
- Platforms like AWS IoT, Azure IoT, and Google Cloud IoT provide infrastructure for device management, real-time processing, and scalable storage.
- Utilize real-time analytics for alerts and monitoring and batch analytics for identifying trends and training models.
- Store structured sensor data in time-series or NoSQL databases.
- Ensure the architecture scales horizontally to support growing device counts and data volumes.
Cloud design must prioritize reliability, scalability, and secure integration with third-party systems.
4. Application Layer: User Interface and Dashboards
This is the user-facing component—usually a web or mobile app.
- Displays live data, historical trends, alerts, and device controls.
- Must support secure command execution (e.g., toggle devices, set thresholds).
- Design for clarity: Utilize graphs, maps, and real-time status indicators to present device data effectively.
- Support multi-platform access (iOS, Android, web) and user roles (admin, viewer, etc.).
- API integration is crucial for connecting with cloud services and managing data flow securely.
Well-structured UIs enhance usability, enable faster decision-making, and minimize support overhead.
Before you build, you need a clear plan. Let’s define your IoT goals and map out your requirements.
Planning Your IoT Application (Objectives, Requirements, Monetization)
Effective planning defines what you’re building, who it’s for, and how it creates value. Before diving into IoT application development, this phase aligns business goals with technical direction.
Define Use Cases and Business Objectives
Begin with a clear understanding of the specific challenges addressed by your IoT app and its unique value proposition.
- Clarify use cases: Are you improving industrial efficiency, building a smart home system, or enabling remote health monitoring?
- Identify primary users: Consumer apps and enterprise systems have different functional expectations.
- Define measurable goals: Examples include “reduce unplanned downtime by 20%” or “enable real-time tracking of medical assets.”
These objectives guide your feature set, technical design, and KPIs for success.
Market Research and Target Audience
Understand who you’re building for and what already exists.
- Validate your idea through market research.
- Identify your target audience, such as homeowners, logistics managers, clinicians, etc.
- Study competitors to uncover feature gaps and pricing benchmarks.
- Research industry-specific requirements: healthcare (HIPAA, FDA), automotive (ISO 26262), etc.
This input helps prioritize features and informs compliance planning early.
Monetization Models and Business Strategy
Choose how the application will generate revenue or value.
- Device Sales: Sell hardware as a one-time purchase.
- Subscription Services: Charge monthly for app features or cloud access.
- Usage-Based Billing: Monetize based on frequency, usage time, or data volume.
- Data Monetization: With proper consent, offer aggregated data insights to third parties.
- Hybrid Models: Combine models—for example, device sales plus a premium subscription tier.
Additionally, plan for post-sale support, firmware updates, and cloud maintenance, as these are ongoing operational expenses.
Functional and Non-Functional Requirements
Create a detailed Software Requirements Specification (SRS) covering:
Functional Requirements:
- What data devices collect and how often?
- What users see on dashboards and what controls they have.
- System behaviors include real-time alerts, user-device interactions, and automation rules.
- Third-party integrations (e.g., ERP, health records).
Non-Functional Requirements:
- Scalability: Plan for growth to thousands of devices or users without needing major redesigns.
- Performance: Set acceptable latency limits for live updates or commands (e.g., under 2 seconds).
- Security & Privacy: Define encryption needs, authentication, secure device onboarding, and applicable compliance (e.g., GDPR, HIPAA).
- Reliability & Offline Support: Specify local caching, edge processing, or fallback behaviors for limited connectivity.
- Compatibility: Define platform support (iOS, Android, Web), device interoperability, and API integrations.
Get input from engineers and stakeholders to ensure coverage from both technical and business perspectives.
If you’re still shaping your requirements, a quick strategy workshop with DEVtrust can help clarify the next steps.Get in touch with DEVtrust today!
After defining your goals, focus on choosing technologies tailored to your specific IoT needs.
Choosing the Right Tech Stack and Tools
Once your requirements are precise, choose hardware, software, and protocols that match your use case, scalability needs, and technical constraints.
IoT Hardware Selection (Devices & Sensors)
Select devices and sensors that align with your application’s environment and data requirements.
- Sensor Types: Match hardware to required metrics (e.g., temperature, motion, GPS).
- Durability: Utilize industrial-grade components for harsh environments and medical-grade components for healthcare use cases.
- Compatibility: Ensure microcontrollers and sensors support the needed protocols (e.g., BLE, I2C, UART).
- Power Efficiency: For battery-powered devices, select low-power components and communication modules (e.g., BLE, Zigbee).
- Scalability: Pick MCUs that can handle multiple connections and inputs if scaling is expected.
- Firmware Support: Choose hardware with reliable SDKs, active communities, and documentation.
Common Options:
- Arduino, ESP32, STM32 – for embedded applications.
- Raspberry Pi, NVIDIA Jetson – for edge processing and ML.
- Particle, Arduino IoT boards – for built-in connectivity and faster prototyping.
Evaluate cost, support, and power consumption, especially if manufacturing at scale. Don’t forget to budget for test equipment and staging units.
IoT Platforms and Middleware
Use an IoT platform to simplify connectivity, device management, and data routing.
- Popular Platforms: AWS IoT Core, Azure IoT Hub, Google Cloud IoT, IBM Watson, ThingsBoard.
- Protocol Support: Ensure support for MQTT, HTTP, CoAP, and other protocols, as well as SDKs for your hardware.
- Scalability & Cost: Platforms often bill by message volume—project your device count and message rate.
- Data Processing: Select platforms with built-in analytics, stream processing capabilities, or rule engines.
- Device Management: Look for features like OTA firmware updates, health monitoring, and remote configuration.
- Security & Compliance: Choose platforms that provide encryption, device identity management, and certifications, such as ISO 27001 or SOC 2.
Also consider middleware components like:
- MQTT brokers (e.g., Mosquitto)
- API gateways
- Time-series databases (e.g., InfluxDB)
Achieve HIPAA/GDPR‑compliant architecture with a security audit from DEVtrust:Security & QA Testing Services
Networking and Communication Protocols
Choose protocols based on power, range, bandwidth, and environment.
Device-to-Gateway/Device-to-Cloud Options:
- Wi-Fi: High bandwidth; power-intensive. Best for fixed, powered devices.
- Bluetooth Low Energy (BLE): Low power, short range. Ideal for wearables and indoor sensors.
- Cellular (4G/5G): Great for mobile or remote deployments. Higher power consumption and cost.
- LPWAN (LoRaWAN, NB-IoT, Sigfox): Long-range, low power, low data rate. Ideal for smart city or agriculture use cases.
- Mesh Networks (Zigbee, Z-Wave, Thread): Useful for smart buildings with many short-range devices.
- Industrial Protocols: Use Modbus, CAN, or Ethernet in manufacturing and factory settings.
Message Protocols:
- MQTT: Lightweight, ideal for unreliable or low-bandwidth networks.
- HTTP/REST: Simple but less efficient; used where direct communication is needed.
- CoAP: Similar to REST but optimized for constrained devices.
- AMQP: Suited for complex, enterprise-grade messaging.
Ensure interoperability or plan for protocol bridges at the gateway layer.
Development Tools, Languages, and Frameworks
Select development tools that align with your team’s skill set and app complexity.
Device Side:
- Languages: C/C++ for microcontrollers; Python for SBCs like Raspberry Pi.
- Tools: Use vendor SDKs, serial debuggers, protocol analyzers, and simulators.
Backend:
- Languages/Frameworks: Node.js, Python (Django/Flask), Java (Spring), Go.
- Architecture: Use microservices for scalability and event-driven handling.
Frontend:
- Web: React, Angular, Vue.
- Mobile: React Native, Flutter (cross-platform); Swift/Kotlin for native apps.
- Real-time Updates: Utilize WebSockets, MQTT, or push notifications to deliver live data streams.
Storage & Databases:
- Time-Series: InfluxDB, TimescaleDB – ideal for sensor logs.
- NoSQL: MongoDB, DynamoDB – for flexible data models.
- Cloud Object Storage: For raw files or multimedia data.
Analytics & AI:
- Use TensorFlow Lite or NVIDIA Jetson for edge inference.
- Cloud options include AWS SageMaker, Azure ML, and BigQuery, providing scalable analytics capabilities.
Build on AWS IoT, Azure IoT Hub, or GCP — check out our backend & cloud architecture services:Backend & Cloud Solutions.
With your stack in place, it’s time to walk through the development process from start to finish.
IoT App Development Process (Step-by-Step)
Creating a production-ready IoT application involves multiple disciplines: software engineering, hardware programming, backend/cloud development, and system testing. Here’s a step-by-step breakdown of the IoT application development process:
Step 1: Design the User Experience and Prototype
Start with clear UI/UX and system flow designs.
- User Interface: Create wireframes that show key screens, including device lists, dashboards, alerts, controls, and settings.
- Onboarding Flows: Design how users add new devices (QR code, Bluetooth, Wi-Fi setup).
- Prototyping Tools: Use Figma or Adobe XD to build clickable mockups.
- Early Feedback: Share prototypes with users or stakeholders to validate workflows and navigation.
- System Prototype: Set up a minimal working demo (one sensor, cloud, app) to test device-cloud-app connectivity and validate stack choices.
This early design phase helps catch usability or architecture issues before full-scale development.
Step 2: Develop the IoT Device Software (Embedded Programming)
Write the firmware that runs on the physical device.
- Sensor & Actuator Code: Use GPIO, I2C, or SPI to read sensors and trigger actuators—leverage vendor SDKs where available.
- Connectivity Logic: Use MQTT or HTTP clients to send data to the cloud. Implement buffering and retry mechanisms to prevent data loss in the event of connection failures.
- Edge Processing: Include logic for on-device decision-making, such as threshold-based alerts or lightweight ML models designed to operate efficiently on limited hardware resources.
- Security: Store credentials securely, encrypt data in transit (TLS) and implement secure boot or signed firmware updates.
- OTA Updates: Include logic to receive and install firmware updates over the air.
Design firmware to be modular and testable, enabling simulation of inputs and easy debugging.
Step 3: Build the Application Backend and API
Develop server-side systems that process data, run business logic, and expose APIs to the front end.
- Data Ingestion: Accept messages via MQTT or HTTP. Use queues or stream processors to manage the load.
- Business Logic: Implement rules for triggering alerts, aggregating stats, and processing device inputs. Define rules clearly: e.g., “If the device sends an SOS message, notify all users in that device’s group via push notification.” The backend should enforce these rules reliably.
- Storage: Use time-series databases for sensor data and relational databases for user/device metadata. Structure data for fast querying.
- APIs: Build REST or GraphQL APIs for historical data. Use WebSockets or MQTT for real-time updates.
- IoT Platform Integration: If using AWS IoT, Azure IoT Hub, etc., configure device communication and utilize cloud-native services (such as Lambda or DynamoDB) where possible.
Ensure services are secure, scalable, and follow a clear separation of concerns.
Step 4: Develop the Front-End Application (Web/Mobile)
Build a user-facing app that displays data and allows device control.
- UI Implementation: Use the prototype as a guide to implement dashboards, controls, alerts, and settings.
- Real-Time Data: Use WebSockets or MQTT for real-time sensor updates. For less dynamic data, polling may suffice.
- Control Commands: Let users send commands through the app. Backend services relay them to the device via MQTT or APIs.
- Offline Mode: Implement local caching and queuing to ensure app usability during network disruptions.
- Testing and Feedback: Conduct usability tests with real users to identify interface issues, onboarding gaps, or unclear workflows.
Use charting libraries (e.g., D3.js, Chart.js) to visualize data clearly and responsively.
Step 5: Integration and System Testing
Once all components are built, test the entire system together.
- Functional Testing: Verify data flow from device to cloud to app and command execution from app to device.
- Interoperability: Test multiple device types, platforms, and OS combinations for compatibility.
- Performance Testing: Simulate high loads to evaluate backend performance and latency. Scale resources as needed.
- Security Testing: Perform penetration testing on devices, APIs, and cloud services. Encrypt traffic (TLS/HTTPS), enforce authentication and scan for known vulnerabilities.
- Usability Testing: Have non-technical users try onboarding and operating the system. Simplify unclear steps.
Use automated test pipelines and continuous integration to catch issues early. Treat testing as an ongoing effort, not a one-time phase.
Building functionality is one thing—protecting your data and devices is another. Here’s where security steps in.
Prioritizing Security and Data Compliance
Security and privacy are foundational to IoT application development and must be integrated into the architecture from day one, not added as an afterthought.
IoT Security Best Practices
Due to the distributed nature of devices and hardware limitations, securing IoT systems requires a layered approach.
1. Device Security
- Assign unique credentials to each device; avoid default usernames or passwords.
- Use secure boot and firmware signing to ensure only verified code runs.
- Maintain an OTA update system to regularly patch vulnerabilities.
- For high-risk environments, utilize hardware security modules (HSMs) or trusted execution environments (TEEs) to ensure secure operations.
2. Data Encryption
- Encrypt all data in transit with TLS/SSL.
- If devices are resource-constrained, consider using lightweight encryption or secure gateways for encrypted tunneling.
- Encrypt sensitive data at rest in cloud storage, especially for personal or location data.
3. Authentication and Access Control
- Enforce strong authentication for users; use multi-factor authentication (MFA) where necessary.
- Devices should authenticate using certificates or secure tokens—never basic auth or unsecured endpoints.
- Apply role-based access control (RBAC) in your backend to isolate customer data.
4. Secure APIs
- Protect APIs from injection attacks and misuse.
- Implement rate limiting, input validation, and strict authentication tokens.
- Secure third-party integrations with the same rigor as internal endpoints.
5. Network Security
- Isolate IoT devices using VPCs, VLANs, or dedicated subnets.
- Monitor traffic for anomalies, such as unexpected outbound communication.
- Use firewalls, VPNs, or zero-trust architectures to limit unauthorized access.
6. Regular Security Updates
- Schedule and automate updates across devices, mobile apps, and backend services.
- Track and respond to new CVEs or vendor security disclosures.
- Maintain a vulnerability management process with clear patch deployment procedures.
IoT systems are frequently targeted—devices often face thousands of attack attempts per month. Establishing a proactive, well-documented security strategy not only mitigates risk but also builds credibility with enterprise customers and regulated industries.
Certifications such as ISO/IEC 27001 or IoT-specific frameworks can further enhance your trust profile.
Beyond security, compliance with global data laws ensures your app is both lawful and trustworthy.
Data Privacy and Regulatory Compliance
If your IoT application collects personal or sensitive data, regulatory compliance is not optional—it must be addressed from the earliest development stage. Non-compliance with laws such as GDPR or HIPAA can result in fines, lawsuits, and a loss of user trust.
Understand Applicable Laws
Start by identifying which regulations apply based on the regions you operate in and the type of data you collect.
- GDPR applies to personal data from EU residents. It mandates clear consent, data minimization, the right to access, and the right to be forgotten.
- HIPAA governs protected health information (PHI) in U.S. healthcare systems and applies strict rules on how patient data is stored, transmitted, and accessed.
- CCPA applies to California users and emphasizes user rights around data disclosure, deletion, and opt-outs.
- Industry-specific standards may also apply (e.g., PCI DSS for payment data, ISO 26262 for automotive, or FDA regulations for medical devices).
Map these laws to your system architecture and feature set early in development to avoid retrofitting compliance later.
Design for Data Minimization
Collect only the data you need to deliver core functionality.
- Avoid gathering personal identifiers unless essential.
- For example, a predictive maintenance sensor doesn’t need employee names or emails.
- Fewer data points reduce your attack surface and simplify compliance audits.
This principle aligns with GDPR’s mandate for data minimization and reduces overall exposure.
User Consent and Transparency
Make consent explicit and meaningful.
- Clearly explain what data you collect, why, and how it will be used.
- Use opt-in checkboxes for non-essential data collection.
- Provide privacy settings within the app, such as toggles for location tracking or third-party data sharing.
- Maintain detailed logs of consent and user preferences to comply with audit requirements.
A well-designed consent workflow helps prevent violations and improves user trust.
Secure Data Handling
Security is foundational to regulatory compliance.
- Encrypt all personal and sensitive data both at rest and in transit using industry-standard protocols (e.g., AES-256, TLS 1.2+).
- Apply role-based access controls (RBAC) to ensure only authorized systems or users access protected data.
- Maintain audit logs for data access and changes.
- Follow secure development practices, including static code analysis and penetration testing for vulnerabilities.
- Use secure enclaves or trusted execution environments when dealing with extremely sensitive data like medical records.
Cloud providers with SOC 2, ISO 27001, or HIPAA-compliant certifications can strengthen your baseline, but they don’t eliminate your responsibilities.
Retention and Deletion Policies
You must define how long data is stored and when it’s removed.
- Don’t store IoT data indefinitely without a purpose. Create data lifecycle policies.
- Implement automatic deletion or anonymization after a specific period.
- Provide functionality for users to request deletion of their data (Right to Erasure) or download their data in portable formats (Right to Portability) as per GDPR.
Clearly documenting these rules will also help during compliance audits.
Monitoring and Incident Response
Prepare for data breaches before they happen.
- Set up anomaly detection systems and intrusion monitoring.
- Create an incident response plan with clear responsibilities and escalation paths.
- Know your reporting obligations—GDPR, for instance, requires notification of a breach to authorities within 72 hours.
- Regularly rehearse breach scenarios and refine your response based on those drills.
Choose cloud platforms with built-in logging, monitoring, and compliance support—but don’t assume they handle everything for you.
Make Compliance Part of the Development Lifecycle
Treat privacy and compliance as functional requirements—not afterthoughts.
- Include regulatory checklists in your sprint planning and QA cycles.
- Conduct privacy impact assessments (PIAs) during feature planning.
- Document how data flows through your system, from collection to storage and deletion. This documentation helps during external audits or legal reviews.
- Perform security and privacy-focused code reviews, not just functionality tests.
Building compliance into your development process protects users, builds credibility, and reduces long-term technical and legal risk.
After securing your app, focus on deploying it reliably and scaling it to meet demand without breaking.
Deployment, Scalability, and Resilience
Deploying an IoT application goes beyond just shipping the code. You need to plan for how the system will run in production, scale as your user base grows, and stay resilient in the face of failures. Effective IoT application development anticipates these factors from the start.
Cloud Deployment and Infrastructure Setup
Most IoT systems run on the cloud for scalability and availability. Set up your production environment with reliability and repeatability in mind:
- Cloud Infrastructure: Choose a provider (AWS, Azure, GCP) or hybrid model. Use Infrastructure-as-Code tools (Terraform, CloudFormation) to manage and replicate environments reliably.
- Modular Deployment: Deploy services like data ingestion, APIs, and analytics as containers (Docker) or serverless functions. Use orchestration tools (Kubernetes, AWS ECS) for scaling and availability across regions.
- IoT Platform Integration: Managed IoT platforms handle core connectivity. You’ll still need to deploy custom services and verify them in staging before going live.
- Database Scaling: Choose scalable databases with support for clustering and read replicas. Partition time-series data and enable auto-scaling for high-volume ingestion.
- Security: Use VPCs, store credentials securely, and limit network exposure to only necessary endpoints.
With proper infrastructure and isolation in place, your IoT app can run securely and scale predictably.
Ensuring Offline Functionality and Resilience
Downtime is inevitable—design your system to handle it gracefully.
- Edge Processing: Devices or gateways should support basic functions offline. For example, smart hubs can continue automation even when disconnected.
- Data Caching and Sync: Use store-and-forward methods. Cache data locally and sync when connectivity resumes. For apps, show cached data with a timestamp when real-time access is unavailable.
- Redundancy: Avoid single points of failure. Use multiple cloud instances with load balancers. In the field, add backup connectivity like cellular fallbacks.
- Graceful Degradation: Ensure the app functions in limited mode if parts of the system fail. Show alerts like “Data is delayed” instead of crashing.
- Monitoring and Alerts: Track uptime, latency, and error rates. Set alerts for connectivity drops, firmware issues, or processing lags to respond quickly.
Scalability and Future Growth
IoT applications often scale quickly. Plan for expansion from the start.
- Distributed Architecture: Use microservices and stateless services to scale individual components like data ingestion or analytics as needed.
- Cloud Auto-Scaling: Serverless and managed services can scale with traffic. Use these for bursty or unpredictable loads.
- Data Management: Archive historical data to cheaper storage. Use cloud lifecycle rules and pipelines to manage retention and cost.
- Load Testing: Simulate growth regularly to find system limits. Monitor CPU, memory, IOPS, and database throughput to plan capacity upgrades.
- Operational Scaling: Build scripts and automation for device onboarding, bulk firmware updates, and large-scale monitoring. Automate customer provisioning and support workflows as the system grows.
- Interoperability: Use standard protocols to support future hardware and prevent vendor lock-in.
Versioning and Continuous Improvement
Evolving your IoT application requires structured updates and feedback loops.
- API Versioning: Introduce new API versions (e.g., /v2/) to support upgrades without breaking existing devices.
- Firmware Management: Track and manage firmware versions. Enable rollbacks if issues arise during OTA updates. Use staged rollouts for safer deployments.
- App Updates: Keep mobile/web apps updated through app stores. Notify users of major changes and include release notes when functionality changes.
- Feedback and Iteration: Collect usage data and user feedback to prioritize future improvements. Treat deployment as the starting point for ongoing enhancement.
This approach keeps your IoT system stable while allowing it to evolve without major disruption.
Once deployed, managing devices throughout their lifecycle is key to long-term performance and uptime.
Device Lifecycle Management and Maintenance
Practical IoT applications require ongoing management of both software and hardware. A solid device lifecycle plan ensures performance, security, and customer satisfaction over time.
Provisioning and Onboarding Devices
Scaling deployments demand a smooth onboarding process for new devices. Key elements include:
- Unique Identity Provisioning: Assign each device a unique ID and credentials at the time of manufacture or setup. Devices should securely register with your cloud platform using keys or certificates during onboarding. Most IoT platforms offer provisioning services for this.
- Onboarding Workflow: Design a user-friendly setup experience. Standard methods include scanning QR codes or using BLE-based Wi-Fi configuration. Clear in-app instructions or documentation are essential to reduce support issues.
- Batch Deployment Tools: For large deployments, script the onboarding process to handle device registration and verification efficiently (e.g., onboarding hundreds of sensors in a factory).
Well-designed onboarding minimizes friction for users and simplifies scaling.
Monitoring and Remote Diagnostics
After deployment, continuous monitoring helps maintain system health.
- Heartbeat Signals: Devices should regularly check-in, sharing statuses like battery level, signal strength, and uptime. Alerts should trigger if a device goes silent.
- Fleet Monitoring Dashboards: Track key metrics—uptime, error rates, data throughput—to detect issues early, such as firmware bugs affecting multiple devices.
- Remote Diagnostics: Enable remote access for logs and test commands to troubleshoot issues without on-site visits. Some IoT platforms support remote actions and health checks.
This setup ensures high service levels and faster issue resolution.
OTA Firmware Updates and Patches
Firmware updates are imperative for long-term security and functionality.
- Efficient Delivery: Use cloud URLs or MQTT chunks to deliver firmware. Optimize large files with delta updates.
- Fault Tolerance: Ensure updates can resume or retry if interrupted to avoid incomplete installations.
- Version Tracking: Monitor firmware versions across the fleet (e.g., 1,000 on v1.2, 500 on v1.3) via the dashboard.
- Staged Rollouts: Deploy updates in phases (e.g., 5%, then 20%, then 100%) to catch issues early and limit impact.
- Rollback Support: Retain the previous firmware until the new one boots successfully. Enable automatic fallback if the update fails.
- User Notification: Inform users of upcoming reboots or downtime; allow scheduling for mission-critical devices.
Inform users about update schedules, especially when devices must reboot or pause operations.
Device Health and End-of-Life
Plan for device aging, failure, and replacement:
- Maintenance Alerts: Set reminders for calibration or regular service for devices like sensors.
- Replacement Strategy: Let users swap out a device and retain its data profile without full reconfiguration.
- Decommissioning: Securely retire devices—remove them from active systems, wipe data, and update licensing or subscriptions. Archive historical data if needed.
Proper lifecycle management prevents security risks from unused devices and avoids system clutter.
A complete lifecycle approach—from provisioning to decommissioning—keeps your IoT deployment secure, scalable, and reliable over time.
Managing OTA, fleet monitoring, and decommissioning? Let DEVtrust handle full device lifecycle orchestration – from onboarding to end-of-life.
Conclusion
Creating an IoT application demands more than technical know-how—it requires a methodical approach to IoT application development, emphasizing precision in architecture, security, and user experience from the outset. Every step, from defining objectives to managing device lifecycles, has a direct impact on scalability, performance, and long-term success.
Building something complex with real-time logic and platform integrations? DEVtrust brings the right blend of experience and execution. Our team of experienced IoT app developers builds robust, production-grade systems tailored to your goals. Connect with us to build IoT solutions that work.
How to Create an IoT Application: Full Development Guide
Master IoT application development: define goals, secure designs, select hardware, and integrate cloud. Create smart solutions now!
Contact Us